Kolide: 'Are You Worse at Security Than the TSA?'

You know the drill: when you go through airport security there are two lines. In one, a TSA agent makes sure you're the person in your passport photo. In the other, a machine scans your carry-on for explosives, weapons, or a normal-sized bottle of shampoo.
Enterprise security is much the same, but instead of passengers and luggage, we're talking about end users and their devices. In the first line, user authentication verifies a user's identity, and it's gotten pretty sophisticated in the past few years, with SSO and MFA becoming more common.
But user devices don't get nearly the same level of attention. The average device trust solution only looks at a handful of endpoint security factors, like OS updates and firewall. If this really were the TSA, that wouldn't even be an x-ray machine, more like holding a bag to your ear and listening for a ticking sound.
And that's assuming an organization looks at end user devices at all. Kolide's Shadow IT report found that 47% of companies let unmanaged devices access their resources, and authenticate via credentials alone.
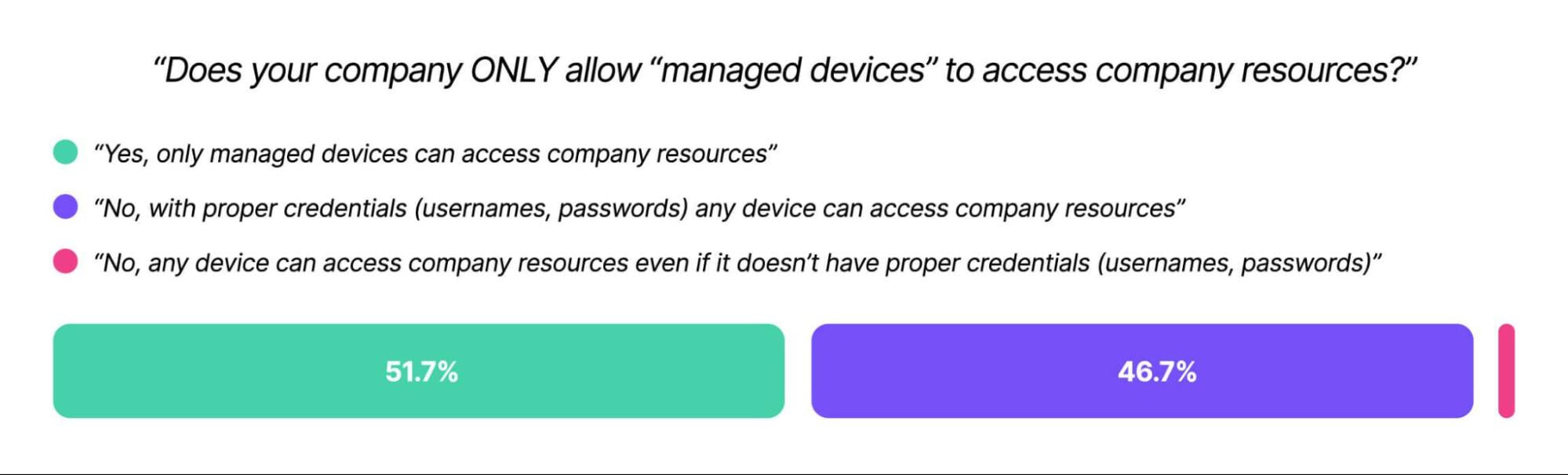
Unmanaged devices (those outside a company's MDM) can be infected with malware, full of PII, or worse -- they can belong to a bad actor using phished employee credentials.
And hey, there are valid reasons for a device not to be enrolled in MDM. Contractor devices, Linux machines, and employee phones all need to be able to access company resources. But there's plenty of room for middle ground between "fully locked down and managed" and an open-door device policy.
Specifically, companies need device trust solutions that block devices from authenticating if they don't meet minimum security requirements.
Even with phishing-resistant MFA, it's frighteningly easy for bad actors to impersonate end users -- in the case of the MGM hack, all it took was a call to the help desk. What could have prevented that attack (and so many others) was an unspoofable form of authentication for the device itself.
That's what you get with Kolide's device trust solution: a chance to verify that a device is both known and secure before it authenticates. Kolide's agent looks at hundreds of device properties (remember, our competitors only look at a handful). What's more, our user-first, privacy-respecting approach means you can put it on machines outside MDM: contractor devices, mobile phones, and even Linux machines.
Without a device trust solution, all the security in the world is just security theater. But Kolide can help close the gaps. (And we won't even make you take off your shoes.)
